I had to integrate Exchange Online with an on-premise DLP system for one of my customers. The goal was that all messages delivered to the Internet must go through a deployed on-premise DLP server.
By default, even if a classical hybrid is deployed, all messages sent to the Internet by cloud mailboxes are delivered by Exchange Online directly to the recipient server. To achieve my goal, I had to override the standard logic.
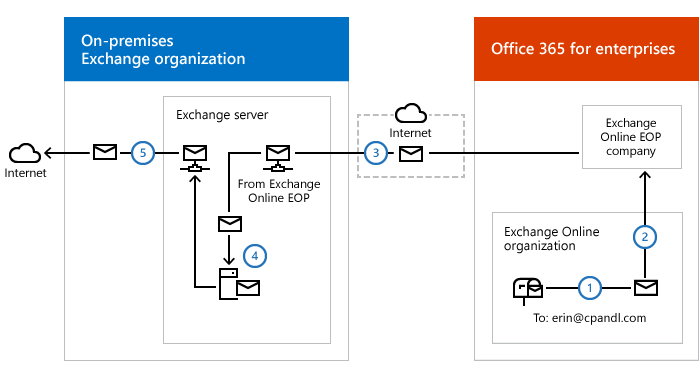
The logic had to be:
- A user with a mailbox in the Exchange Online organization sends a message to an external Internet recipient.
- Exchange Online is configured to send all Internet-bound messages to an on-premises server, so the message is routed to an on-premises Exchange server.
- The on-premises Exchange server sends the message to the internal DLP system.
- The internal DLP system checks and forwards all the messages to an internal mail gateway.
- The internal mail gateway looks up the MX record for the recipient domain and sends the message to the recipient’s mail servers on the Internet.
The centralized mail transport option can help with this; this option can be enabled during HCW setup.
With centralized mail transport, you can route all mail from mailboxes in the Exchange Online organization through the on-premises organization before they’re delivered to the Internet.